September 20, 2022
4 Min Read

Security and Risk Leaders Can Use Report to Understand how Absolute’s Unique Resilience and Self-Healing Capabilities Ensure Always-On ZTNA
The modern work-from-anywhere environment is defined by distributed employees and connected partners, security skills shortages, and advanced cyberthreats. As these factors and others collide to drive complexity and risk, organizations are demanding innovations that not only reduce the possibility of breaches and defend against disruptive attacks, but also improve performance and end user experiences.
Challenges Zero Trust Addresses
To address challenges, organizations are increasingly turning to Zero Trust (ZT). This strategic approach to defending enterprise networks calls for limiting the level of access granted to users and devices across systems and data to only those that are positively verified. This “need-to-know” approach to networks and information provides greater assurance that data will remain protected against attackers and that systems will be subjected to fewer cyber-related disruptions.
Zero Trust was introduced in 2010 by Forrester analyst John Kindervag. Over the years, it has given rise to a raft of technologies that support the approach. These span Cloud Security Access Brokers (CASB), Secure Access Services Edge (SASE) platforms, Micro Segmentation, multi-factor authentication tools, and Zero Trust Network Access (ZTNA) solutions, just to name a few.
ZTNA Delivers Security, Efficiency, and Performance
Of all these technologies, ZTNA is coming to be accepted as the pillar that enables end users to leverage their devices to access systems and data with the highest level of security, efficiency, and performance. The challenge that enterprise security and risk leaders now face isn’t whether ZTNA is right for them, but rather how to select, deploy, and manage a ZTNA solution that will help them to overcome their organizations’ unique set of obstacles while scaling to meet growing demands.
Security ZTNA Leaders
To help organizations identify leading ZTNA offerings, global analyst firm KuppingerCole published the 2022 Leadership Compass: Zero Trust Network Access report. Complete with a historical overview and an in-depth analysis of what effective ZT and ZTNA delivers, it includes an objective and unbiased review of the Absolute Software Secure Access product portfolio, our integrated ZTNA solution. Powered by our patented Persistence® technology, it not only delivers secure access and improved end user experiences, but also a level of resilience and self-healing that ensures maximum performance while reducing down time and eliminating opportunities for internal and external threats to tamper with or turn off the application.
Zero Trust Network Access is based on the assumption that any network is always hostile, and thus, any IT system, application, or user is constantly exposed to potential external and internal threats.
Zero Trust Network Access is based on the assumption that any network is always hostile, and thus, any IT system, application, or user is constantly exposed to potential external and internal threats.
ZT architectures require proper authentication and authorization for each session involving users, applications, networks (including clouds), and data.
ZT architectures require proper authentication and authorization for each session involving users, applications, networks (including clouds), and data.
As opposed to traditional network-centric architectures, ZTNA platforms work completely independently from the underlying hardware, appliances, switches, or other network devices.
As opposed to traditional network-centric architectures, ZTNA platforms work completely independently from the underlying hardware, appliances, switches, or other network devices.
A fundamental difference between modern ZTNA and legacy VPN solutions is the separation of control and data planes, which can be set up in different environments and still enable a single point of management and visibility across complex deployments.
A fundamental difference between modern ZTNA and legacy VPN solutions is the separation of control and data planes, which can be set up in different environments and still enable a single point of management and visibility across complex deployments.
Connecting an end-user device to a ZTNA platform requires an agent, a piece of software not dissimilar from a traditional VPN client.
Connecting an end-user device to a ZTNA platform requires an agent, a piece of software not dissimilar from a traditional VPN client.
Absolute’s internal research shows that both cloud and on-prem security applications are subject to disruptions driven by technology issues and tampering, sometimes falling well below the required level of performance needed to maintain effective levels of security and compliance. With our Persistence technology extended into our ZTNA solution, our customers experience up-time that well exceeds industry and compliance standards to reduce the risk of costly and disruptive security incidents and data breaches.
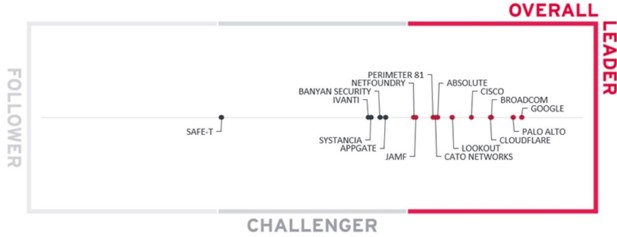
How Absolute Ranks
Named as an “Overall Leader” in the report, KuppingerCole reviewed us among a field of 13 competitors, which it evaluated for all-around functionality, innovation, market presence, and financial position.
Notably, KuppingerCole analyst Alexei Balaganski called attention to both Absolute’s security and performance capabilities:
Additionally, the report gave Absolute a “5 out of 5” rating for Security, Deployment, and Interoperability, along with a “4 out of 5” rating for Functionality and Usability. Key strengths recognized are:
In addition to being named an overall leader, the Absolute Secure Access ZTNA solution is recognized as a leader in four additional report categories, including Product, Innovation, Market, and Technology.
Read the Report
To read the full report and learn more about why the Absolute Secure Access product line may be right for your organization’s ZTNA requirements and how it stacks up against top competitors, download here.
*Noted by Absolute Software internal analytics, not mentioned in the published report.
Share this article