May 22, 2023
5 Min Read

Having a toolbox with multiple tools is not as valuable as having one with the right tools. This fact is especially true in cybersecurity, where a security breach can cause vendors to come knocking, each with their own promises about how their product can prevent disaster.
Delivering ROI in enterprise security, however, is about more than preventing attacks; it is also about minimizing business disruption by remediating the impact of an attack as quickly as possible. For today’s organizations, this has made application resilience a critical building block for durable cyber defenses.
Overconfidence Equals Under Protected
Increasing security spending is a natural reflex after an attack. However, spending without a smart strategy can lead to yet another crisis—a budgetary one that ends with you in front of the board of directors, unable to demonstrate how the security tools you said to purchase are providing extra value. The truth is, buying more tools can often have a negative side effect—creating a false sense of security and additional complexity.
Late last year, Gartner predicted spending on information security and risk management products and services worldwide would grow more than 11% to $188.3 billion in 2023. Our 2023 Resilience Index- A False Sense of Security Imperils Digital Enterprises found that enterprise work-issued laptops typically have more than 11 security applications installed. We also discovered that it is common to have more than one application present to address endpoint management, anti-malware, and encryption.
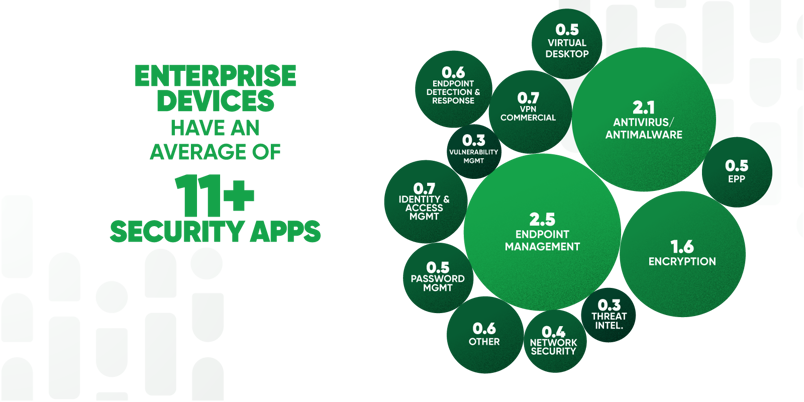
While this type of redundancy can be presented as creating multiple layers of security for better protection, the truth is it also increases complexity. Each of these applications must be added to the list of software and hardware that needs to be managed and kept up to date to ensure effectiveness and overall functionality. Any gaps in patching can lead to devices falling out of alignment with security policies and opportunities for attackers.
Out-of-date configurations can lead to security policies that contradict one another. In the 2023 Resilience Index report, our analysis revealed that 25-30% of the devices we analyzed in our report had unhealthy security controls. An “unhealthy” security control is one that may be installed, but not running properly, or intentionally disabled, or conflicted with the multitude of software patching that naturally happens as part of proper vulnerability management. As the controls’ effectiveness erodes over time, users may try to circumvent them altogether.
Let’s consider this from a regulatory compliance perspective for a moment. If an assessor asks your organization to verify the controls it has in place on every device accessing sensitive data, can you do it? What would you find? Could you even locate sensitive data across a fleet of remote endpoints?
The transition to remote work where employees and contractors access IT resources from distributed locations has only complicated matters. Visibility and control challenges abound as IT teams seek to identify and remediate issues for mobile users leveraging devices with varying patch levels to access enterprise resources from outside networks. For example, while most enterprise devices in our report run Windows 10, it was not uncommon for patch levels to be months behind. The worst offender was the government sector, where Windows 10 patches were an average of 214 days old. That’s not great news when zero-day attacks and rapid proof-of-concept exploits move to real-world exploitation in days, not months.
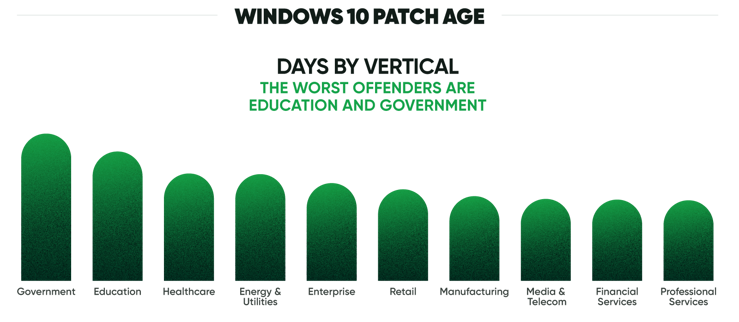
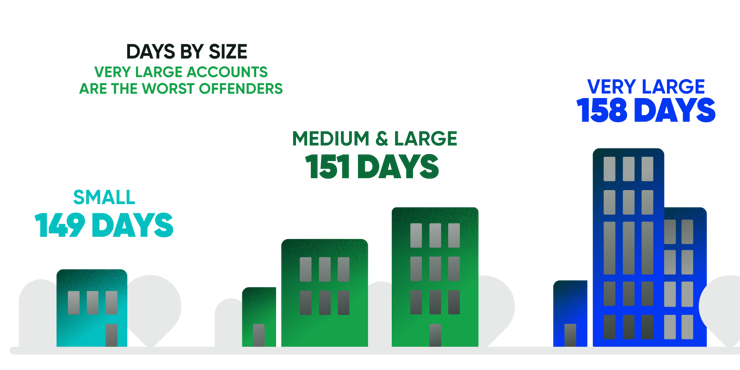
Spread this problem across the dozens of applications on the typical enterprise device, and the scope of the problem becomes evident. Security requires visibility and the capacity to fix vulnerabilities when they appear, but enterprise IT teams have their hands full with devices that often have more than 60 different applications of various types. Each of those apps has its updates, which must be installed to reduce risk. Existing software-only tools just cannot seem to keep pace.
Complexity and security have always had a rocky marriage, and between the realities of supporting a distributed workforce and the need to secure significant numbers of devices and applications, it is time for a divorce. Today’s enterprises need a different approach, one that empowers them to maintain visibility into the health of devices and applications so security holes can be closed as soon as they emerge.
Application Resilience Builds Better Defenses
In short, they need their security to be resilient. Enterprise applications and devices have to be resistant to software decay and malicious attacks. At Absolute, we use our Persistence technology, which is already embedded in the firmware of devices built by the world’s top system manufacturers, to maintain unbreakable visibility and control of the endpoints our clients use. We build on that Absolute Application Resilience to monitor application hygiene and automatically repair and/or reinstall unhealthy third-party applications to remediate any issues.
The real-world implications of this are powerful. Take the various security tools installed on the typical endpoint, for example. Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Remote Access solutions all play a pivotal role in your ability to prevent and, in some cases, respond to cyber incidents. As part of the 2023 Resilience Index report, we analyzed the application health of the tools our customers were using from security vendors in the EPP, EDR, and Remote Access spaces who are cited as leaders in industry reports, specifically: Citrix, Cisco, CrowdStrike, Microsoft, Netskope, Palo Alto Networks, SentinelOne, Sophos, Trend Micro, and Zscaler. We then compared the results after applying Application Resilience policies. Here are the anonymized results in random order:
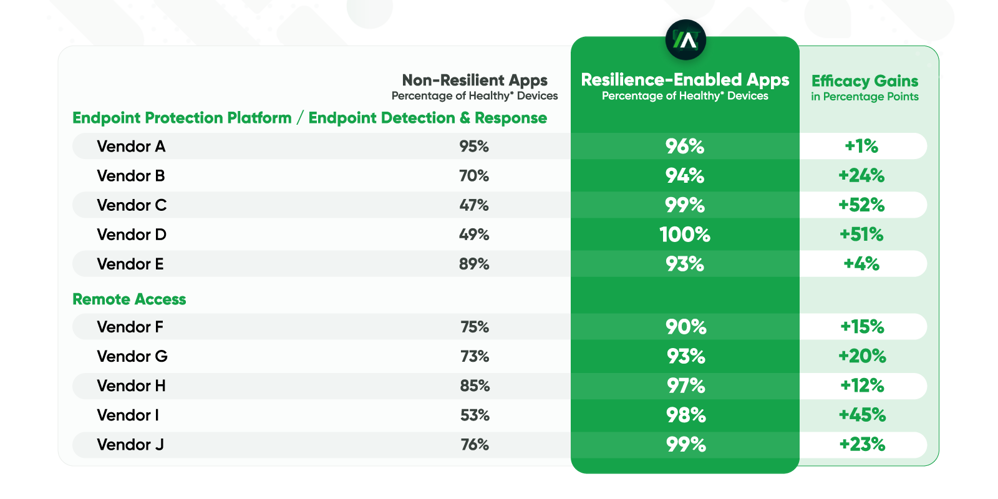
Applying this level of visibility and control across different applications helps employees stay secure and productive regardless of location. Any problems that are detected can be repaired automatically. Application resilience replaces a false sense of security stemming from the size of your security budget with true confidence rooted in the knowledge that your organization can overcome the damage done by software decay and threat activity. By focusing on application resilience, leaders can reduce the risk of business disruption and provide their users with higher levels of security assuredness, finally winning the battle of security and complexity with resilience.
To learn more about how a false sense of security imperils digital enterprises, read our 2023 Resilience Index.
Share this article