April 27, 2023
4 Min Read

Numerous cyberattacks and data breach headlines keep reminding us that cyber security is fragile. The work-from-anywhere model exacerbates the strain on IT and security teams because the common perimeter defense has diminished. Absolute’s telementry data published in our 2023 Resilience Index shows a 15% growth of enterperise device locations. This means employees are now performing significant work on networks their organizations do not own or control, which dramatically increases an organization’s risk exposure.
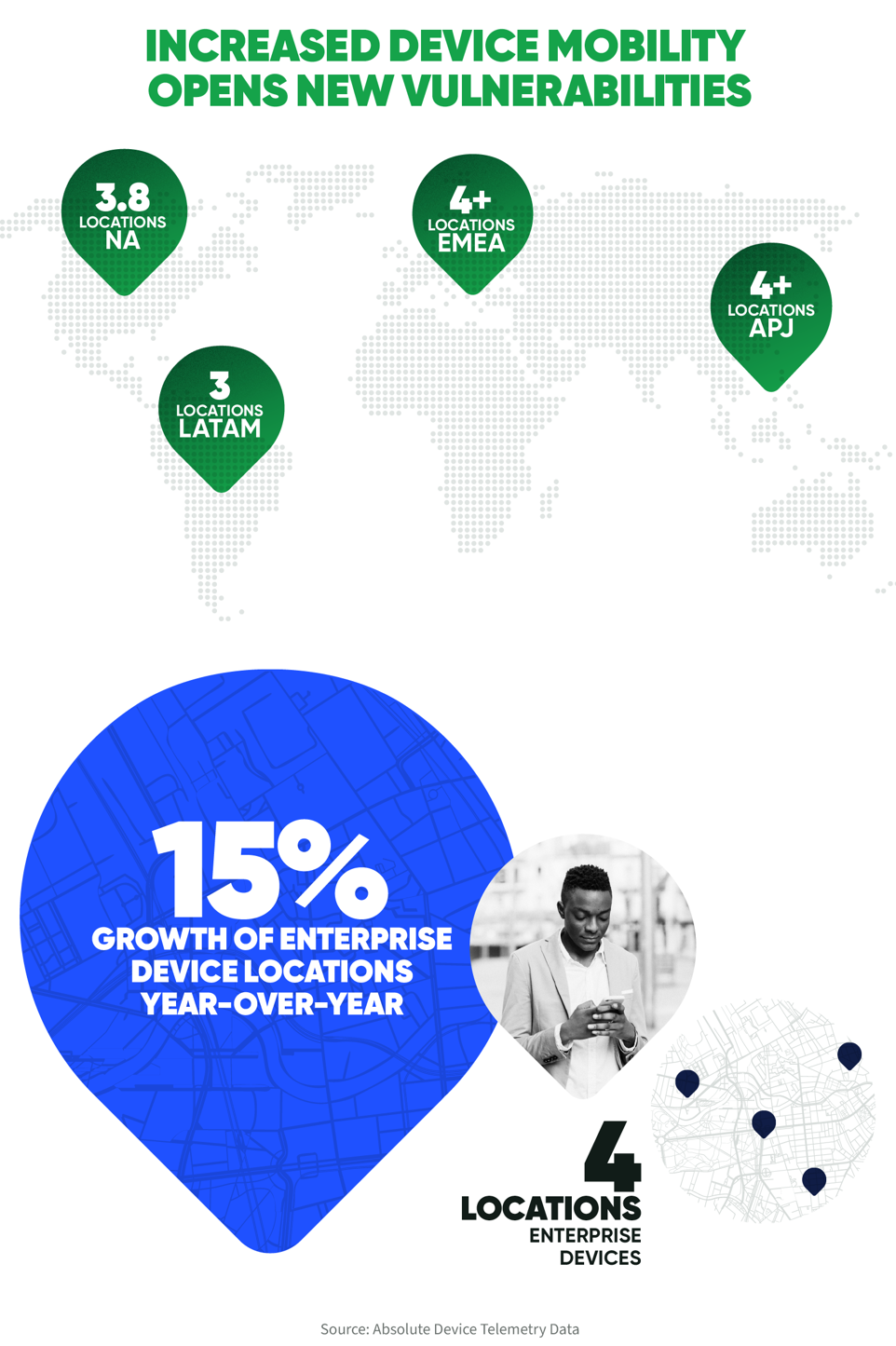
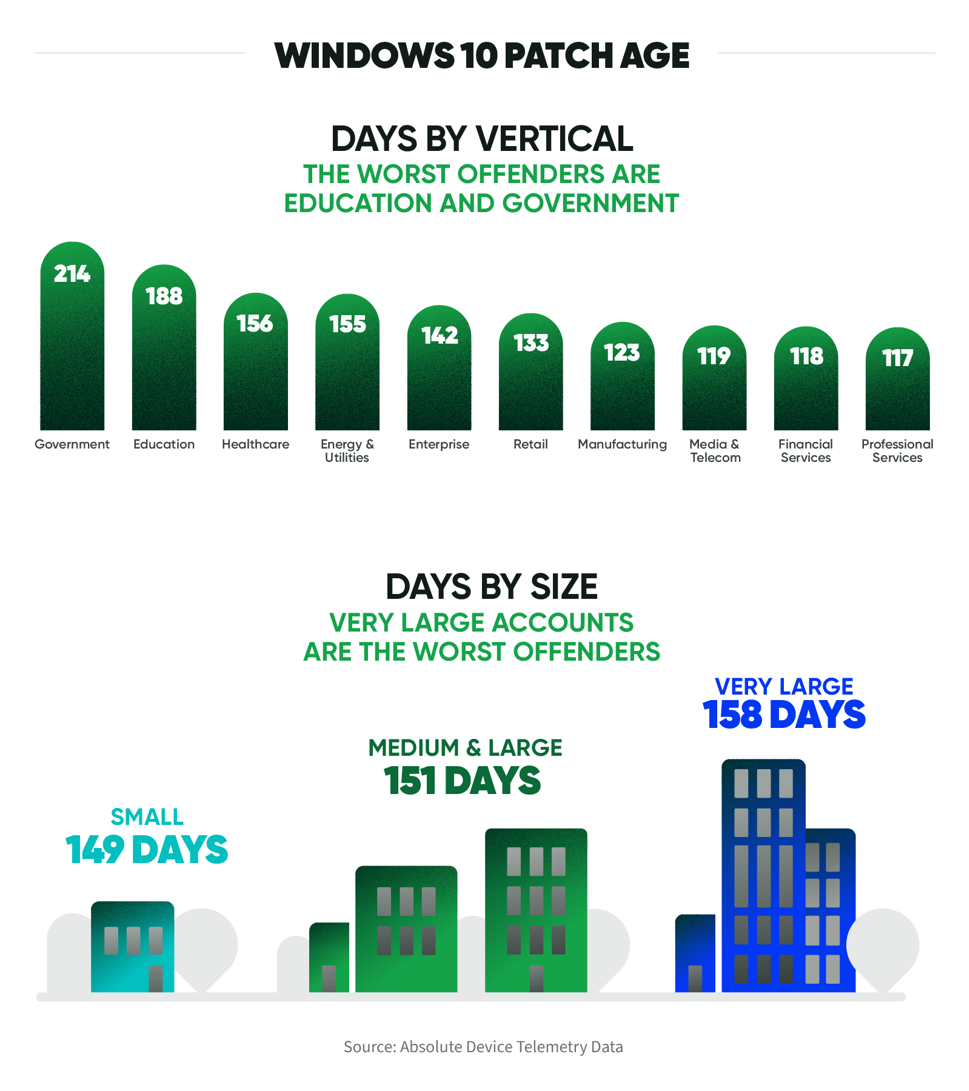
In addition, existing device health and security challenges are compounded by a broad mix of networks, hardware, OS versions, and patches. For example, our telementry data shows that 94% of enterprise devices are on Windows 10, and the patch age for the largest accounts is as old as 158 days.
As a result, organizations are looking for ways to connect their employees to corporate networks and resources securely. This is driving a new ‘comply to connect’ trend that balances security and cyber resilience to ensure your employees can confidently get to work and keep working, no matter where risk finds them.
This means that instead of exclusively focusing efforts on preventing an attack, it’s essential to develop a plan to reduce the impact when a successful attack occurs. This is why many forward-thinking organizations are adopting a new strategy to cope with today’s increased cyber threats, called cyber resilience.
Cyber resilience aims to ensure that an adverse cyber event, whether intentional or unintentional, does not negatively impact the confidentiality, integrity, and availability of an organization’s business operation.
One method for enterprises to evaluate their cyber resilience is through these lenses: complexity, compliance, and continuity.
Complexity
Complexity focuses on application health and includes the number of endpoint controls, the number of devices and users, and the number of operating systems. You can ask these questions to assess your state of endpoint, device, and OS complexity:
Compliance
Compliance is the scorecard that focuses on risk and encryption. You can ask these questions to learn more about your state of compliance:
Continuity
Continuity includes mobility, app health, and availability. You can ask these questions to learn more about your state of continuity:
In the fourth year of our recurring research of endpoint resilience trends, we analyzed anonymized data from 14 million Absolute-enabled devices active across customer organizations in North America, Europe, and APAC, as well as data and information from trusted third-party sources.
This report examines the state of resiliency in the work-from-anywhere model by assessing its complexity, continuity, and compliance posture. The findings affirm that despite the long-standing belief that deploying more security solutions will result in greater protection against threats, the truth of the matter is very different.
Read the 2023 Resilience Index to learn how to assess complexity, compliance, and continuity in your environment and evaluate your cyber resilience posture.
Share this article